
Inside TA397’s Playbook - From Phishing Emails to RATs
TA397, also known as UAC-0001, uses phishing emails, malicious macros, and Remote Access Trojans (RATs) to target high-profile entities, primarily in Ukraine.

Inside Operation Digital Eye - How Hackers Used Legitimate Tools for Infiltration
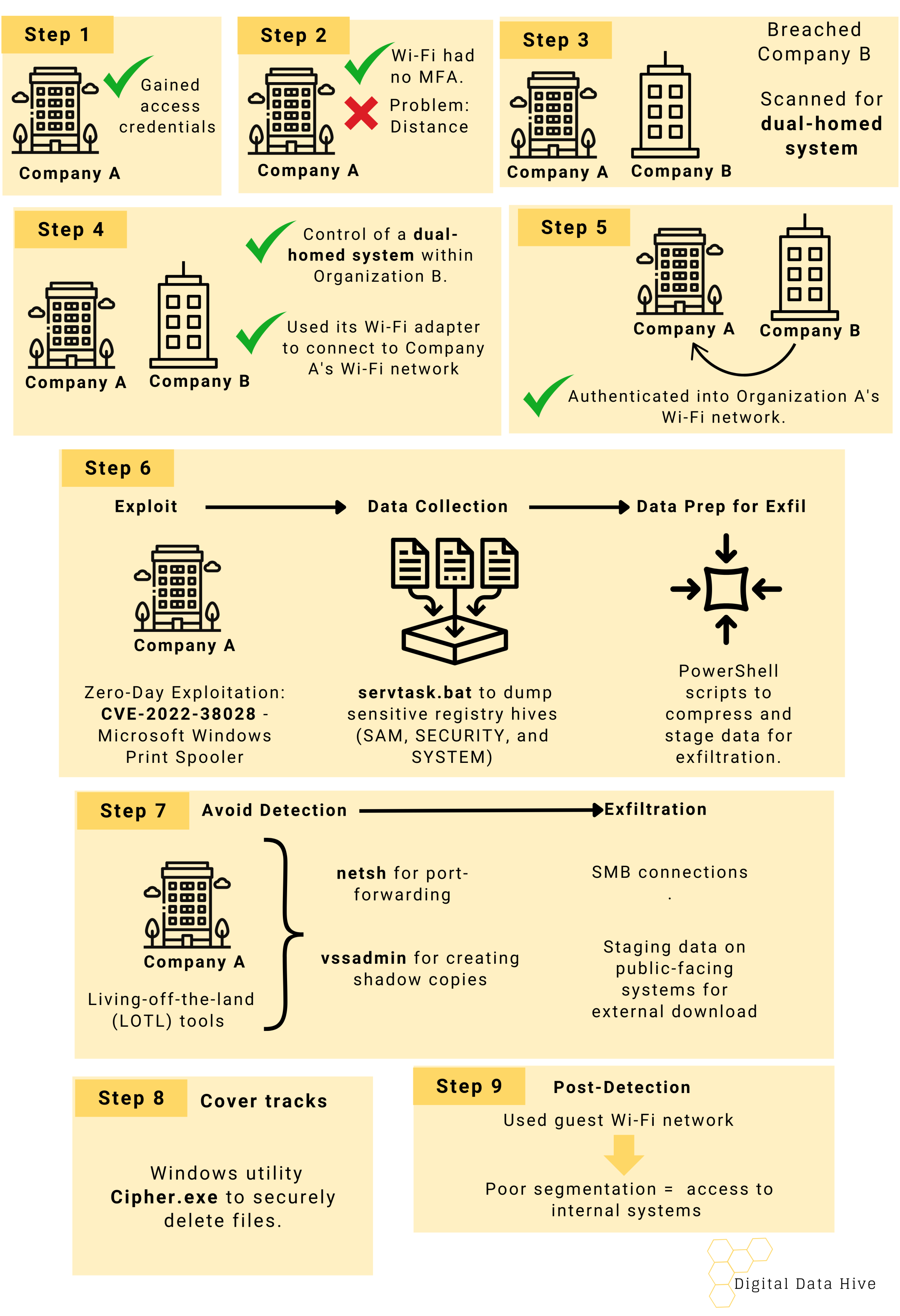
The Breach from Next Door. How Russian APT Exploited Wi-Fi to Infiltrate Their Target
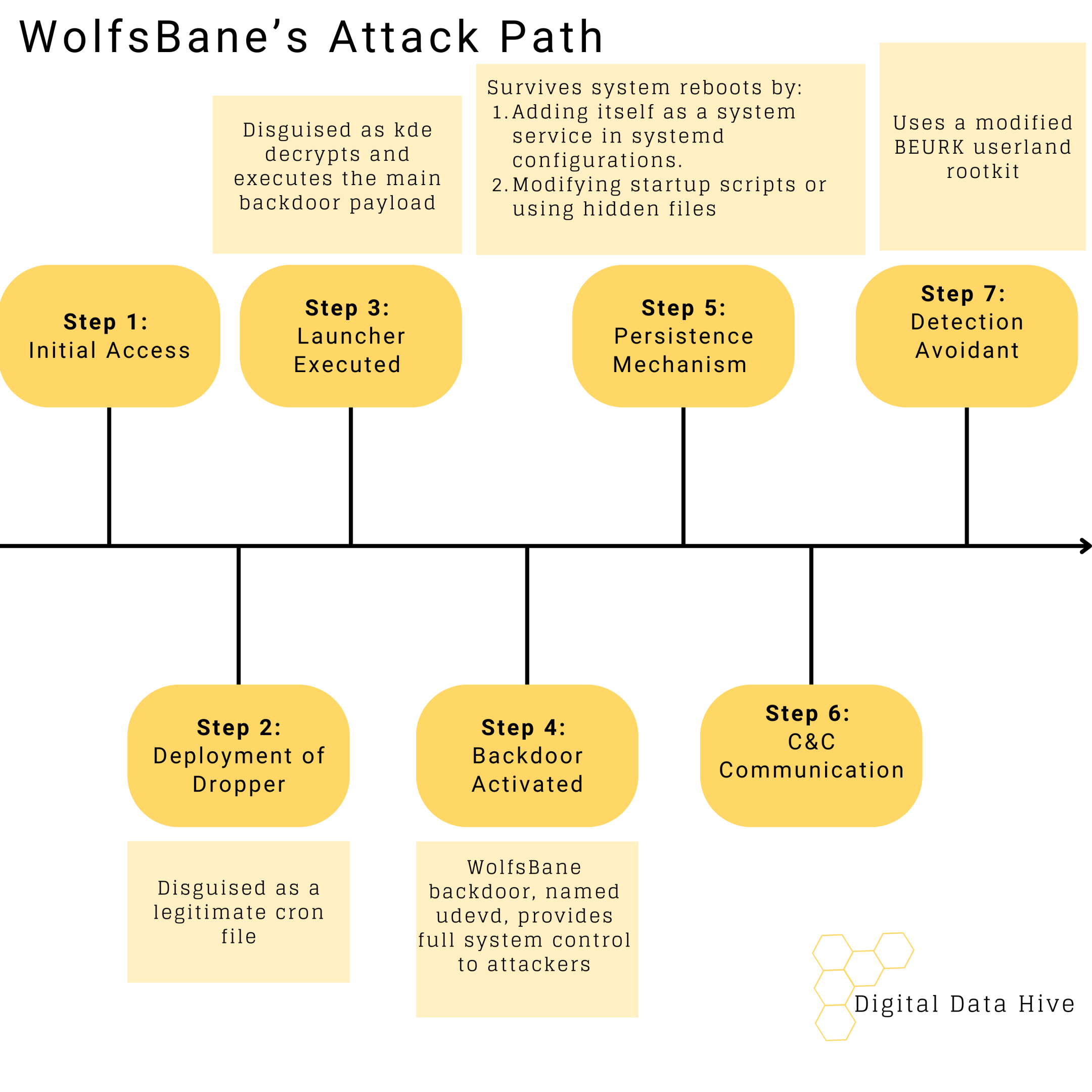
Beware the Wolf- WolfsBane Marks Its Linux Territory

Fortinet VPN Flaw: How Hackers Can Sneak Past Security Without a Trace

T-Mobile Breached Again: A Closer Look at Salt Typhoon’s Espionage Tactics

Did Apple Lie to Us? The Truth Behind M-Series Chips' Security Promises.

Scattered Spider is Causing Arachnophobia

Elevating Cybersecurity with NIST CSF 2.0

Cybersecurity - A Pillar of Modern Business - According to the CISA

Understand your Network - Simplifying Netstat with the Network Top Processes Program!

